Social Engineering Tactics: Recognizing and Defending Against Cyber Threats
In an age where technology is integrated into nearly every aspect of our lives, cybercriminals have developed increasingly sophisticated tactics to exploit human psychology. Social engineering is a critical component of many cyber attacks, relying on manipulation rather than technical skills to deceive individuals into divulging sensitive information. Understanding these tactics is essential for organizations and individuals alike to defend against potential threats. This article explores common social engineering tactics and offers strategies for recognition and defense.
Understanding Social Engineering
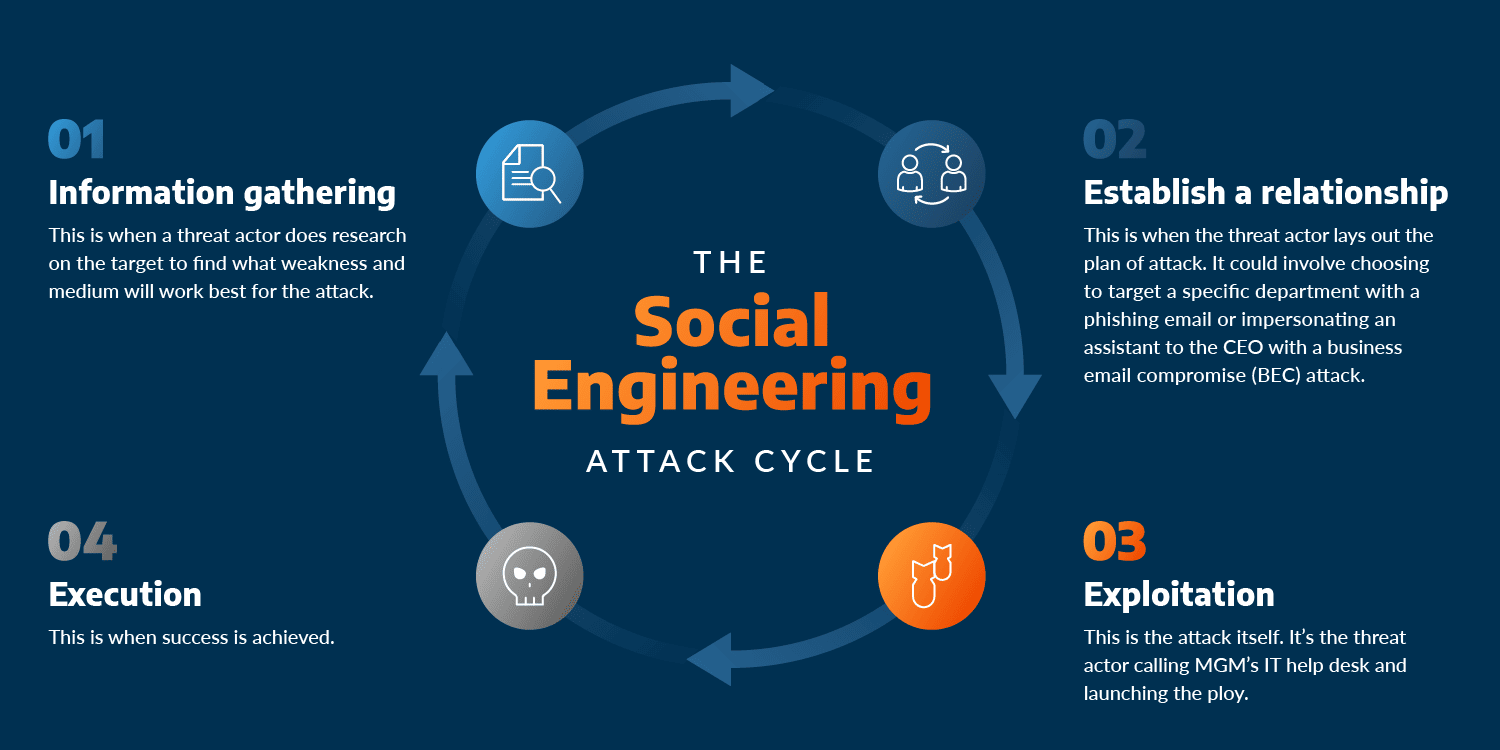
Social engineering refers to psychological manipulation techniques used by attackers to trick individuals into providing confidential information or performing actions that compromise security. Unlike traditional hacking, which often focuses on exploiting technical vulnerabilities, social engineering targets the human element, making it a potent threat.
Common Social Engineering Tactics
1. Phishing
Phishing is perhaps the most well-known social engineering tactic. It typically involves fraudulent emails or messages that appear to come from reputable sources. These messages often urge recipients to click on malicious links or provide sensitive information, such as login credentials or financial details. Variants include spear phishing, which targets specific individuals or organizations, and whaling, which targets high-profile executives.
2. Pretexting
Pretexting involves creating a fabricated scenario to steal personal information. Attackers may pose as a trusted entity, such as a bank or a technical support representative, to extract sensitive information from victims. The pretext is often convincing, making it difficult for the victim to recognize the deceit.
3. Baiting
Baiting involves enticing individuals with a promise of something appealing, such as free software or media, to trick them into downloading malware. Attackers might leave infected USB drives in public places, hoping that someone will plug them into their computer, thereby granting access to the attacker.
4. Tailgating
Tailgating, also known as “piggybacking,” occurs when an unauthorized person follows an authorized individual into a restricted area. This tactic exploits the social norms of politeness, as individuals often feel uncomfortable denying access to someone who appears to have legitimate reasons for entry.
5. Quizzes and Surveys
Cybercriminals may use seemingly harmless quizzes or surveys to gather personal information. These can appear on social media platforms or through email, asking for details that can later be used to breach accounts or steal identities.
Recognizing Social Engineering Attempts
Awareness is the first line of defense against social engineering attacks. Here are some indicators to help recognize potential threats:
- Unusual Requests: Be cautious of unsolicited communications requesting sensitive information, especially if they create a sense of urgency.
- Check URLs: Hover over links to reveal their true destination. Phishing emails often use deceptive URLs that mimic legitimate websites.
- Look for Red Flags: Poor grammar, spelling mistakes, and generic greetings (e.g., “Dear Customer”) are common in phishing attempts.
- Verify Requests: If you receive an unusual request, verify it directly with the organization or individual through trusted contact methods.
Defending Against Social Engineering Threats
1. Employee Training
Organizations should invest in regular training sessions to educate employees about social engineering tactics. Employees who understand the risks are more likely to recognize and report suspicious activities.
2. Implement Security Policies
Establish clear security policies regarding data access, communication, and incident reporting. Ensure that all employees are aware of these policies and follow best practices.
3. Use Multi-Factor Authentication (MFA)
Implementing MFA can add an extra layer of security, making it more difficult for attackers to gain access to sensitive information, even if they manage to obtain login credentials.
4. Encourage a Culture of Awareness
Foster an organizational culture that encourages employees to question unexpected requests for sensitive information. Open communication about potential threats can help create a vigilant workforce.
5. Regular Security Audits
Conduct regular audits and assessments of security protocols to identify vulnerabilities and improve defenses against social engineering tactics.
Conclusion
Social engineering remains a significant threat in the realm of cybersecurity, relying on the manipulation of human psychology rather than technical exploits. By understanding common tactics and implementing robust defensive strategies, individuals and organizations can better protect themselves against these deceptive practices. Awareness, education, and proactive measures are crucial in creating a resilient security posture that can withstand the evolving landscape of cyber threats. In a world where cybercriminals are continually adapting their strategies, staying informed and vigilant is the best defense against social engineering attacks.
No Responses